
source: https://www.goodtechthings.com/realization/
Vacation days with no connectivity be like … 😅

Well this is an interesting approach by Google to counter DNS cache poisoning effectiveness.
https://www.theregister.com/2023/01/19/google_dns_queries/
If your DNS queries LoOk liKE tHIs, it’s not a ransom note, it’s a security improvement.
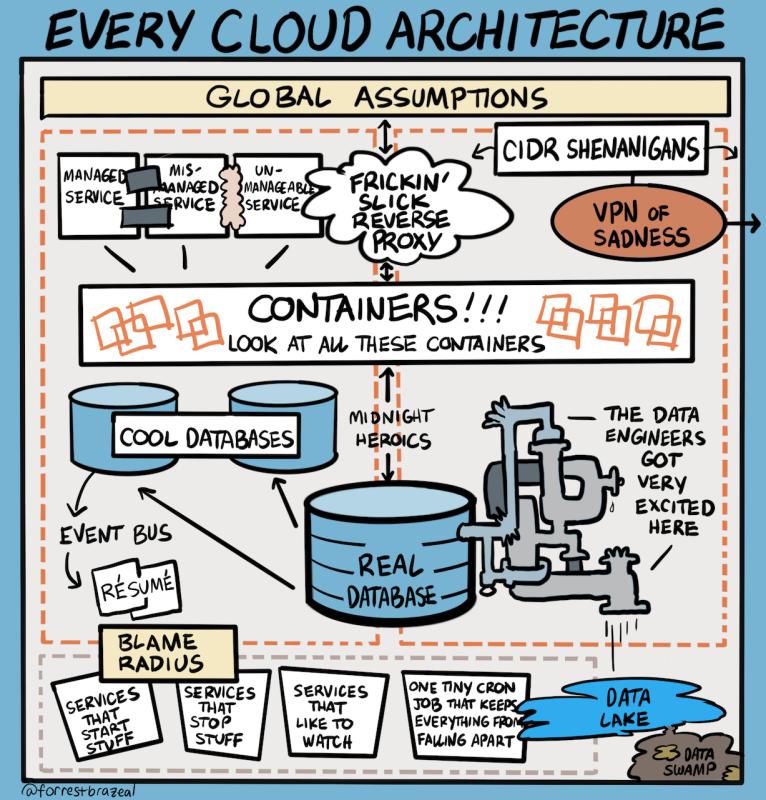
Source: https://www.goodtechthings.com/every-cloud-architecture/
I recall a few environments that fit this narrative 🙂

What systems do security and availability audits cover? A fair question!
Well, the hard truth is that it is your responsibility to identify this as a system owner; and not the duty of an auditor. Don’t sit around waiting for auditors to show up and expect them to answer this question.
Simply put, everything and anything within your ecosystem that may interrupt business continuity should be part of the audit. This can easily include systems that do not even reside in your ‘PROD VPC’, or even be tagged as ‘Production’.
You’ll be surprised how many times it comes down to a small neglected server that sits in the corner and very few folk know about, yet holds a critical role in your supply chain processing, or mailing important notifications and updates to clients.
Do a true/practical risk assessment, identify your systems, minimize your exceptions, properly document your findings, and present them as the lay of the land; your auditors will be very thankful.

In many cases, key pointers towards success are hidden in a sequence of undesirable outcomes.
Continue reading Error is Good!Benefits of being multilingual in the world of technology: Passwords are so simple to remember, yet meet every password complexity policy being 12 characters long, alphanumeric, Upper case, and special characters 😄

Company: “Our data is encrypted at rest, and in transit. We are SOC2 assessed and HIPAA compliant. Our Cyber team conducts quarterly audits, our Security Ops are 24/7, and our employees go through quarterly security training.”
That one developer about to run a wild query exporting all data to a CSV file: “Hold my beer!”
Invest in Data Access Controls
Does your establishment handle sensitive communication on daily basis? Are you looking for a secure, no compromise, zero trust, SaaS collaboration suite? Check out wickr; an AWS company.
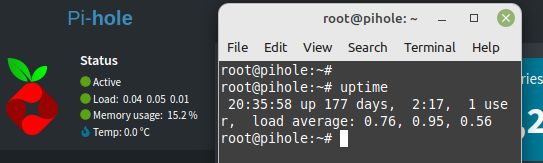
Remember the days when server up-time was how we measured service availability and bragged about it? This Pi-hole DNS server running on a Debian-loaded mini PC at my home office, is now at 177 days since last reboot, yet is fully patched and running latest version of Pi-hole DNS. Maybe it’s because there are no windows near this mini PC 😏